 SOLUTION
SOLUTION
Introduction
With the growth of an every enterprise IT-department and department of Information Security face the task of providing security of information assets. User’s credentials, their identification and key information can be referred to as such assets. For solving such tasks systems of users’ identification and key information management are widely applied.
The main goal of these systems is providing administrators with relevant information about status of user account in different information systems (personnel systems, basic services, etc.) and control over user rights of access to required resources.
List of tasks which can be solved with such systems is wide enough. Here is a short list of them:
- Employee’s entry to the work, granting rights to resources according to his position.
- Transfer to another department, branch or office. Changing access rights.
- Access lock for the time of vacations, sick leave or maternity leave.
- Employee’s dismissal and locking access to resources.
- Granting certificates required for user’s work.
- Renewal and suspension of certificates.
- Accounting of user’s devices.
- Tracking of time and point of access to resources.
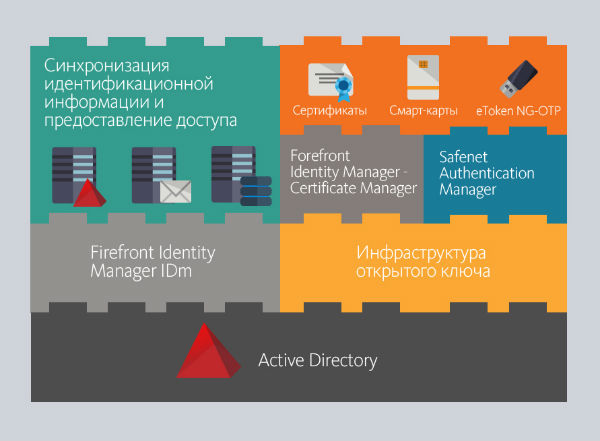
We offer integrated scalable solution consisted of the following components:
- Public Key Infrastructure is a basic solution for developing key information management systems.
- Forefront Identity Manager IDm is a solution for synchronizing and managing user credentials in various personnel databases and Active Directory.
- Forefront Identity Manager Certificate Management allows managing digital certificates of the enterprise. It uses Public Key Infrastructure.
- Safenet Authentication Manager. This solution allows monitoring all the eToken electronic keys and managing content of the keys. The solution can be used together with FIM and PKI and separately as well.
Public Key Infrastructure is a basic solution for developing key information management systems.
Forefront Identity Management IDm is a solution for synchronizing and managing user credentials in various personnel databases and Active Directory.
Forefront Identity Manager Certificate Management allows managing digital certificates of the enterprise. It uses Public Key Infrastructure.
SafeNet Authentication Manager. This solution allows monitoring all the eToken electronic keys and managing content of the keys. The solution can be used together with FIM and PKI and separately as well.
This solution can be represented as following structure:
Public Key Infrastructure
The solution is based on certificates of x.509 v 3 standard which are based on technology of RSA asymmetric encryption and 3DES and SHA encryption algorithms.
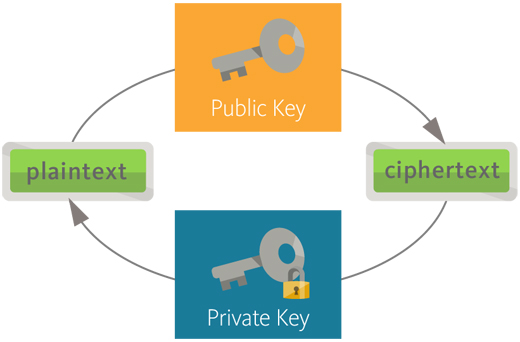
The main idea of Public Key Infrastructure is that critical data are protected with encryption. Extensive use of encryption for protected information traffic is surely requires solving the task of reliable keys distribution. Just to solve this task asymmetric encryption – system with public key – was created. Asymmetry is when there are two keys: one of them is private key and the second one is public key. They are liked with special mathematical dependence, which ensures impossibility to restore private key if public key is available. That’s why public key may be distributed to anyone without any risk. Thus, systems with public key allow transferring only public information without transferring private key information.
User encrypts massage with receiver’s public key. On receiving the message user decrypts it with his private key.
Considering that many such pairs of keys can be used, methods of keys management and their use control become very important. Just this function is fulfilled by Certification Authorities providing centralizing of keys issuing, distribution, control and cancellation.
Using Public Key Infrastructure at the organization gives the following advantages:
- Protected e-mail. Possibility to sign and encrypt mail messages allows solving problem of non-repudiation and unauthorized access to mailbox (for instance, via OWA).
- Files and folders encryption. It also allows reducing risk of unauthorized access to resources.
- Multi-factor authentication.
- Providing wireless access security.
- Providing remote access security.
- Encrypting web-traffic.
- Providing secure information exchange via network.
Project of Public Key Infrastructure implementation generally has short duration and includes the following stages:
- Research. Analyzing technical and business needs. Gathering information about current infrastructure status.
- Design. Developing and approving project solutions.
- Documenting. Developing required documentation.
- Implementation. Deploying Public Key Infrastructure according to project solutions.
- Operation testing (beta-testing). Aggregating comments and bug fixing.
Our specialists will help to design properly and deploy PKI at your company in a short time and with minimal expenditures.
Forefront Identity Manager Certification Management
Public Key Infrastructure provides powerful platform for issuing digital certificates of wide range of use. Certificates and smart cards allow enhancing information security to a large extent but at the same time management of their life cycle is a complicated and labor-intensive task. The certificate has validity period according to RFC 3208 standard (the validity period is specified by Certification Authority). The more number of certificates is, the more difficult to ascertain when digital identity is expired is. It happens that user retires, loses or deletes his certificate. This also should be monitored. The task of managing these processes is almost infeasible without special software. In this case the enterprise needs centralized solution having the following functionalities:
- User self-service in operations concerning certificates and smart cards.
- System of delegating rights to approve certificates and smart cards issuing to business-managers among others, e.g. direct managers of employees.
- Automated renewal of certificates and smart cards on expiring their validity period.
- Capability to restore certificates and smart cards being lost, to issue duplicates, to suspend their validity and to provide other business scenarios of certificates and smart cards using.
- Notifying employees involved into processes of certificates and smart cards life cycles via e-mail.
- Capability to create various reports showing aspects of certificates and smart cards using.
Such Registration Authority allows significant decreasing workload of Public Key Infrastructure administrators, reducing expenditures for certificates and smart cards management and increasing extent of control over certificates use. All that allows enhancing the whole information security of IT-infrastructure in the long run.
Registration Authority based on Microsoft Forefront Identity Manager Certificate Management allows solving all tasks related to management of certificates and smart cards life cycle. However smart design and implementation of this product is a complicated task. Our knowledge and skills allow carrying this process out with high quality, within a short time, and in full concordance with Customer’s requirements.
Common project of FIM CM implementation includes the following stages:
- Research. Identifying needs, gathering information.
- Design. Creating project solutions.
- Test bed simulating. Deploying project solutions on the test bed.
- Documenting. Creating required documentation.
- Implementation. Deploying project solutions in live environment.
- Operation testing (beta-testing). Aggregating customer’s comments and bug fixing.
Forefront Identity Manager - IdM
SafeNet Authentication Manager
SafeNet Authentication Manager is the most appropriate solution if you have to introduce eToken electronic keys to your enterprise and the number of employees exceeds 50 persons.
In staff increasing and high personnel turnover mistakes during granting or locking access for employees can result in the most negative implications:
- Increasing time period from hiring employee to the beginning of his direct work. Before starting work user should get accesses and passwords to different applications. This process can be represented graphically on the figure given below.
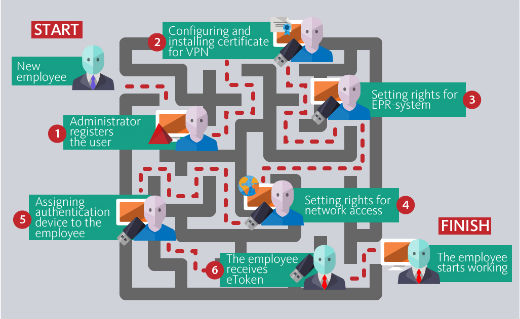
- Using the identity after dismissal for the reason that the administrator has forgotten to lock access of the user.
As a solution for such problems we offer you up-to-date solution based on SafeNet Authentication Manager product.
SAM allows solving such problems and providing the whole functionality by single console.
Following tasks are being solved:
- Management of identification and authentication information from single point. User has not to go through a long procedure of getting access to applications by walking to one administrator after the other.
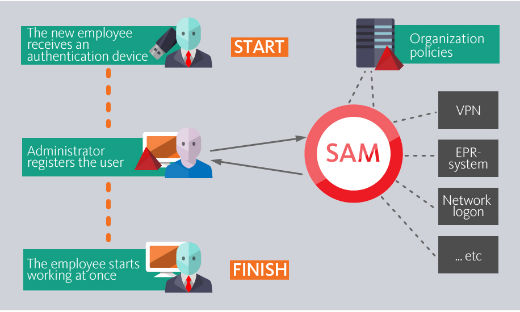
- Getting only those passwords which the user needs for his work. Using mechanisms of connectors and internal policies of SAM deeply integrated with Active Directory allows automated granting access only to the applications which are really required to the user.
- Control over devices. Capability to create reports about devices statuses, their amount and stock balance, etc. allows efficient solving questions of the control over devices using.
Also the solution has following advantages:
- Solution flexibility allows easy implementing different scenarios of system using.
- Integration with Active Directory and AD LDS allows implementing this solution within a short time and bringing it to operation with minimal expenditures.
- The solution uses web-services while working providing administrators with more mobility in management of electronic keys. There appears capability to distribute load among users while solving different problems (updating content, changing PIN, renaming key, etc.).
- Role-based model of SafeNet Authentication Manager allows realizing different scenarios of putting smart card into operation, maintaining it and putting it out of operation.
Standard implementation project includes the following stages:
- Research. At this stage we inspect your infrastructure for availability of SAM implementation.
- Planning. We prepare plan of solution implementation, identify main business-solutions with which integration will be performed.
- Design. We give solution description in technical details.
- Implementation.
- Documentation preparation. At the stage of implementation we prepare required documentation according to the peculiarities of the certain project.
As a result of implementation you get full-featured scalable solution allowing adding new functionality in future.
Key storages
Using smart cards or electronic keys at the enterprise gives the following undeniable advantages:
- Two-factor authentication. To get access user has to have something and to know something. Physical key eToken and its PIN can be such attributes.
- Secure key information storage. Access to key memory can be still made only after PIN input. Locked key information cannot be copied. It can be only deleted.
- Using as a pass. Up-to-date technologies allow implanting RFID chips into card and USB-keys that increases security of your enterprise even more.

Installation of smart cards support is not a big deal. For this you need only to install drivers for card reader and a card itself (for some systems these drivers are included into operating systems) and you can start working.
However for efficient use of the whole functionality of cards all procedures should be described in details:
- Providing the key to the employee
- Updating content of the key (certificates, passwords)
- Employee’s actions in case of key damage
- Employee’s actions in case of key loss
- Employee’s actions in case of retiration
We are ready to offer solution based on electronic keys eToken made by Aladdin R.D. company.
We are ready to provide you with all required regulations so you can use 100% of capabilities of this solution in your organization.
If your company plans to develop then we also recommend you to pay attention to smart cards management systems.
